- hashcat advanced password recovery
- Navigation
- Download
- GPU Driver requirements:
- Features
- Screenshot
- Algorithms
- Attack-Modes
- Supported OpenCL runtimes
- Supported OpenCL device types
- Download older version(s)
- Getting «Exhausted» result even with 100% progress #2328
- Comments
- NimaaaNomaaa commented Mar 13, 2020 •
- ZerBea commented Mar 14, 2020
- NimaaaNomaaa commented Mar 14, 2020
- ZerBea commented Mar 14, 2020
- NimaaaNomaaa commented Mar 14, 2020
- ZerBea commented Mar 14, 2020 •
hashcat
advanced password recovery
Navigation
Download
| Name | Version | Date | Download | Signature |
|---|---|---|---|---|
| hashcat binaries | v6.2.4 | 2021.08.29 | Download | PGP |
| hashcat sources | v6.2.4 | 2021.08.29 | Download | PGP |
Signing key on PGP keyservers: RSA, 2048-bit. Key ID: 2048R/8A16544F. Fingerprint: A708 3322 9D04 0B41 99CC 0052 3C17 DA8B 8A16 544F
Check out our GitHub Repository for the latest development version
GPU Driver requirements:
- AMD GPUs on Linux require «RadeonOpenCompute (ROCm)» Software Platform (3.1 or later)
- AMD GPUs on Windows require «AMD Radeon Adrenalin 2020 Edition» (20.2.2 or later)
- Intel CPUs require «OpenCL Runtime for Intel Core and Intel Xeon Processors» (16.1.1 or later)
- NVIDIA GPUs require «NVIDIA Driver» (440.64 or later) and «CUDA Toolkit» (9.0 or later)
Features
- World’s fastest password cracker
- World’s first and only in-kernel rule engine
- Free
- Open-Source (MIT License)
- Multi-OS (Linux, Windows and macOS)
- Multi-Platform (CPU, GPU, APU, etc., everything that comes with an OpenCL runtime)
- Multi-Hash (Cracking multiple hashes at the same time)
- Multi-Devices (Utilizing multiple devices in same system)
- Multi-Device-Types (Utilizing mixed device types in same system)
- Supports password candidate brain functionality
- Supports distributed cracking networks (using overlay)
- Supports interactive pause / resume
- Supports sessions
- Supports restore
- Supports reading password candidates from file and stdin
- Supports hex-salt and hex-charset
- Supports automatic performance tuning
- Supports automatic keyspace ordering markov-chains
- Built-in benchmarking system
- Integrated thermal watchdog
- 350+ Hash-types implemented with performance in mind
- . and much more
Screenshot
Algorithms
- MD4
- MD5
- SHA1
- SHA2-224
- SHA2-256
- SHA2-384
- SHA2-512
- SHA3-224
- SHA3-256
- SHA3-384
- SHA3-512
- RIPEMD-160
- BLAKE2b-512
- GOST R 34.11-2012 (Streebog) 256-bit, big-endian
- GOST R 34.11-2012 (Streebog) 512-bit, big-endian
- GOST R 34.11-94
- Half MD5
- Keccak-224
- Keccak-256
- Keccak-384
- Keccak-512
- Whirlpool
- SipHash
- md5(utf16le($pass))
- sha1(utf16le($pass))
- sha256(utf16le($pass))
- sha384(utf16le($pass))
- sha512(utf16le($pass))
- md5($pass.$salt)
- md5($salt.$pass)
- md5($salt.$pass.$salt)
- md5($salt.md5($pass))
- md5($salt.md5($pass.$salt))
- md5($salt.md5($salt.$pass))
- md5($salt.sha1($salt.$pass))
- md5($salt.utf16le($pass))
- md5(md5($pass))
- md5(md5($pass).md5($salt))
- md5(md5(md5($pass)))
- md5(sha1($pass))
- md5(sha1($pass).md5($pass).sha1($pass))
- md5(sha1($salt).md5($pass))
- md5(strtoupper(md5($pass)))
- md5(utf16le($pass).$salt)
- sha1($pass.$salt)
- sha1($salt.$pass)
- sha1($salt.$pass.$salt)
- sha1($salt.sha1($pass))
- sha1($salt.sha1($pass.$salt))
- sha1($salt.utf16le($pass))
- sha1($salt1.$pass.$salt2)
- sha1(CX)
- sha1(md5($pass))
- sha1(md5($pass).$salt)
- sha1(md5($pass.$salt))
- sha1(md5(md5($pass)))
- sha1(sha1($pass))
- sha1(sha1($pass).$salt)
- sha1(sha1($salt.$pass.$salt))
- sha1(utf16le($pass).$salt)
- sha256($pass.$salt)
- sha256($salt.$pass)
- sha256($salt.$pass.$salt)
- sha256($salt.sha256($pass))
- sha256($salt.utf16le($pass))
- sha256(md5($pass))
- sha256(sha256($pass).$salt)
- sha256(sha256_bin($pass))
- sha256(utf16le($pass).$salt)
- sha384($pass.$salt)
- sha384($salt.$pass)
- sha384($salt.utf16le($pass))
- sha384(utf16le($pass).$salt)
- sha512($pass.$salt)
- sha512($salt.$pass)
- sha512($salt.utf16le($pass))
- sha512(utf16le($pass).$salt)
- HMAC-MD5 (key = $pass)
- HMAC-MD5 (key = $salt)
- HMAC-SHA1 (key = $pass)
- HMAC-SHA1 (key = $salt)
- HMAC-SHA256 (key = $pass)
- HMAC-SHA256 (key = $salt)
- HMAC-SHA512 (key = $pass)
- HMAC-SHA512 (key = $salt)
- HMAC-Streebog-256 (key = $pass), big-endian
- HMAC-Streebog-256 (key = $salt), big-endian
- HMAC-Streebog-512 (key = $pass), big-endian
- HMAC-Streebog-512 (key = $salt), big-endian
- CRC32
- Java Object hashCode()
- MurmurHash
- 3DES (PT = $salt, key = $pass)
- DES (PT = $salt, key = $pass)
- AES-128-ECB NOKDF (PT = $salt, key = $pass)
- AES-192-ECB NOKDF (PT = $salt, key = $pass)
- AES-256-ECB NOKDF (PT = $salt, key = $pass)
- ChaCha20
- Linux Kernel Crypto API (2.4)
- Skip32 (PT = $salt, key = $pass)
- PBKDF2-HMAC-MD5
- PBKDF2-HMAC-SHA1
- PBKDF2-HMAC-SHA256
- PBKDF2-HMAC-SHA512
- scrypt
- phpass
- TACACS+
- SIP digest authentication (MD5)
- IKE-PSK MD5
- IKE-PSK SHA1
- SNMPv3 HMAC-MD5-96
- SNMPv3 HMAC-MD5-96/HMAC-SHA1-96
- SNMPv3 HMAC-SHA1-96
- SNMPv3 HMAC-SHA224-128
- SNMPv3 HMAC-SHA256-192
- SNMPv3 HMAC-SHA384-256
- SNMPv3 HMAC-SHA512-384
- WPA-EAPOL-PBKDF2
- WPA-EAPOL-PMK
- WPA-PBKDF2-PMKID+EAPOL
- WPA-PMK-PMKID+EAPOL
- WPA-PMKID-PBKDF2
- WPA-PMKID-PMK
- IPMI2 RAKP HMAC-SHA1
- CRAM-MD5
- JWT (JSON Web Token)
- Kerberos 5, etype 17, TGS-REP
- Kerberos 5, etype 17, Pre-Auth
- Kerberos 5, etype 18, TGS-REP
- Kerberos 5, etype 18, Pre-Auth
- Kerberos 5, etype 23, AS-REQ Pre-Auth
- Kerberos 5, etype 23, TGS-REP
- Kerberos 5, etype 23, AS-REP
- NetNTLMv1 / NetNTLMv1+ESS
- NetNTLMv1 / NetNTLMv1+ESS (NT)
- NetNTLMv2
- NetNTLMv2 (NT)
- iSCSI CHAP authentication, MD5(CHAP)
- RACF
- AIX
- AIX
- AIX
- AIX
- LM
- QNX /etc/shadow (MD5)
- QNX /etc/shadow (SHA256)
- QNX /etc/shadow (SHA512)
- DPAPI masterkey file v1
- DPAPI masterkey file v2
- GRUB 2
- MS-AzureSync PBKDF2-HMAC-SHA256
- BSDi Crypt, Extended DES
- NTLM
- Radmin2
- Samsung Android Password/PIN
- Windows Phone 8+ PIN/password
- Cisco-ASA MD5
- Cisco-IOS $8$ (PBKDF2-SHA256)
- Cisco-IOS $9$ (scrypt)
- Cisco-IOS type 4 (SHA256)
- Cisco-PIX MD5
- Citrix NetScaler (SHA1)
- Citrix NetScaler (SHA512)
- Domain Cached Credentials (DCC), MS Cache
- Domain Cached Credentials 2 (DCC2), MS Cache 2
- FortiGate (FortiOS)
- FortiGate256 (FortiOS256)
- ArubaOS
- Juniper IVE
- Juniper NetScreen/SSG (ScreenOS)
- Juniper/NetBSD sha1crypt
- iPhone passcode (UID key + System Keybag)
- macOS v10.4, macOS v10.5, macOS v10.6
- macOS v10.7
- macOS v10.8+ (PBKDF2-SHA512)
- bcrypt $2*$, Blowfish (Unix)
- md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
- descrypt, DES (Unix), Traditional DES
- sha256crypt $5$, SHA256 (Unix)
- sha512crypt $6$, SHA512 (Unix)
- SQLCipher
- MSSQL (2000)
- MSSQL (2005)
- MSSQL (2012, 2014)
- MongoDB ServerKey SCRAM-SHA-1
- MongoDB ServerKey SCRAM-SHA-256
- PostgreSQL
- PostgreSQL CRAM (MD5)
- Oracle H: Type (Oracle 7+)
- Oracle S: Type (Oracle 11+)
- Oracle T: Type (Oracle 12+)
- MySQL $A$ (sha256crypt)
- MySQL CRAM (SHA1)
- MySQL323
- MySQL4.1/MySQL5
- Sybase ASE
- DNSSEC (NSEC3)
- KNX IP Secure — Device Authentication Code
- CRAM-MD5 Dovecot
- SSHA-256(Base64), LDAP
- SSHA-512(Base64), LDAP
- Dahua Authentication MD5
- RedHat 389-DS LDAP (PBKDF2-HMAC-SHA256)
- FileZilla Server >= 0.9.55
- ColdFusion 10+
- Apache $apr1$ MD5, md5apr1, MD5 (APR)
- Episerver 6.x = .NET 4
- hMailServer
- nsldap, SHA-1(Base64), Netscape LDAP SHA
- nsldaps, SSHA-1(Base64), Netscape LDAP SSHA
- SAP CODVN B (BCODE)
- SAP CODVN B (BCODE) from RFC_READ_TABLE
- SAP CODVN F/G (PASSCODE)
- SAP CODVN F/G (PASSCODE) from RFC_READ_TABLE
- SAP CODVN H (PWDSALTEDHASH) iSSHA-1
- PeopleSoft
- PeopleSoft PS_TOKEN
- SolarWinds Orion
- SolarWinds Orion v2
- SolarWinds Serv-U
- Lotus Notes/Domino 5
- Lotus Notes/Domino 6
- Lotus Notes/Domino 8
- OpenEdge Progress Encode
- Oracle Transportation Management (SHA256)
- Huawei sha1(md5($pass).$salt)
- AuthMe sha256
- AES Crypt (SHA256)
- VMware VMX (PBKDF2-HMAC-SHA1 + AES-256-CBC)
- LUKS
- VeraCrypt
- BestCrypt v3 Volume Encryption
- FileVault 2
- VirtualBox (PBKDF2-HMAC-SHA256 & AES-128-XTS)
- VirtualBox (PBKDF2-HMAC-SHA256 & AES-256-XTS)
- DiskCryptor
- BitLocker
- Android FDE (Samsung DEK)
- Android FDE = 10.0
- WBB3 (Woltlab Burning Board)
- PHPS
- SMF (Simple Machines Forum) > v1.1
- MediaWiki B type
- Redmine
- Umbraco HMAC-SHA1
- Joomla = v3.8.5
- bcrypt(md5($pass)) / bcryptmd5
- bcrypt(sha1($pass)) / bcryptsha1
- osCommerce, xt:Commerce
- TOTP (HMAC-SHA1)
- Web2py pbkdf2-sha512
- Django (PBKDF2-SHA256)
- Django (SHA-1)
- Atlassian (PBKDF2-HMAC-SHA1)
- Ruby on Rails Restful-Authentication
- Ruby on Rails Restful Auth (one round, no sitekey)
- Python passlib pbkdf2-sha512
- Python passlib pbkdf2-sha256
- Python passlib pbkdf2-sha1
- PKCS#8 Private Keys (PBKDF2-HMAC-SHA1 + 3DES/AES)
- PKCS#8 Private Keys (PBKDF2-HMAC-SHA256 + 3DES/AES)
- JKS Java Key Store Private Keys (SHA1)
- RSA/DSA/EC/OpenSSH Private Keys ($0$)
- RSA/DSA/EC/OpenSSH Private Keys ($6$)
- RSA/DSA/EC/OpenSSH Private Keys ($1, $3$)
- RSA/DSA/EC/OpenSSH Private Keys ($4$)
- RSA/DSA/EC/OpenSSH Private Keys ($5$)
- XMPP SCRAM PBKDF2-SHA1
- Telegram Desktop = v2.1.14 (PBKDF2-HMAC-SHA512)
- Telegram Mobile App Passcode (SHA256)
- Skype
- MetaMask Wallet
- BitShares v0.x — sha512(sha512_bin(pass))
- Bitcoin/Litecoin wallet.dat
- Electrum Wallet (Salt-Type 1-3)
- Electrum Wallet (Salt-Type 4)
- Electrum Wallet (Salt-Type 5)
- Blockchain, My Wallet
- Blockchain, My Wallet, V2
- Blockchain, My Wallet, Second Password (SHA256)
- Stargazer Stellar Wallet XLM
- Ethereum Pre-Sale Wallet, PBKDF2-HMAC-SHA256
- Ethereum Wallet, PBKDF2-HMAC-SHA256
- Ethereum Wallet, SCRYPT
- MultiBit Classic .key (MD5)
- MultiBit HD (scrypt)
Attack-Modes
- Straight *
- Combination
- Brute-force
- Hybrid dict + mask
- Hybrid mask + dict
- Association *
Supported OpenCL runtimes
- AMD
- Apple
- Intel
- NVidia
- POCL
- ROCm
Supported OpenCL device types
A detailed description of all commandline parameters is available by using --help. Next to that, the 7zip-package contains extensive documentation. Look for examples.txt. If you encounter a Bug, report it in the Forums where Fixes and Beta versions are announced as well.
If you still think you need help by a real human come to #hashcat on Libera.Chat IRC.
Download older version(s)
This is a list of older hashcat versions, it’s not always bad to grab the latest version.
Источник
Getting «Exhausted» result even with 100% progress #2328
Comments
NimaaaNomaaa commented Mar 13, 2020 •
I can’t stand this anymore
the final output is:
Session. hashcat
Status. Exhausted
Hash.Name. WPA-EAPOL-PBKDF2
Hash.Target. dom18 (AP:b0:b2:dc:89:05:2e STA:bc:e1:43:07:e4:ee)
Time.Started. Fri Mar 13 20:49:25 2020 (17 mins, 4 secs)
Time.Estimated. Fri Mar 13 21:06:29 2020 (0 secs)
Guess.Base. File (/mnt/d/stuff/WordList/rockyou.txt)
Guess.Queue. 1/1 (100.00%)
Speed.#1. 9189 H/s (6.13ms) @ Accel:64 Loops:256 Thr:1 Vec:4
Recovered. 0/1 (0.00%) Digests
Progress. 14344384/14344384 (100.00%)
Rejected. 4734913/14344384 (33.01%)
Restore.Point. 14344384/14344384 (100.00%)
Restore.Sub.#1. Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1. $HEX[212121313233343536] -> $HEX[042a0337c2a156616d6f732103]
Im using Ubuntu 16.0 Windows Distributive for this
The code is: ./hashcat -m 2500 -a 0 /mnt/d/stuff/captured.hccapx /mnt/d/stuff/Wordlists/rockyou.txt
I don’t have any error’s coming up when starting a crack
and i ABSOLUTELY have no idea what im doing wrong
The text was updated successfully, but these errors were encountered:
ZerBea commented Mar 14, 2020
- The PSK is not in the wordlist. rockyou.txt is not the best choice.
- the hccapx file is crappy. How did you convert it?
NimaaaNomaaa commented Mar 14, 2020
I’ve made the hccapx file with Wifi-autopwner.
I captured the handshake and used the option «Bruteforce the handshake»
ZerBea commented Mar 14, 2020
As far as I know, Wifi-autopwner runs aircrack suite. That isn’t the best choice in combination with hashcat. Please attach the original cap file to check, if it is ok.
NimaaaNomaaa commented Mar 14, 2020
smh my kali desktop went nuts and i can’t do anything
ZerBea commented Mar 14, 2020 •
No problem. If your desktop is ready again, please do the following steps:
Download hccapx example from here:
https://hashcat.net/misc/example_hashes/hashcat.hccapx
and test it running hashcat:
$ haschcat -m 2500 hashcat.hccapx -a3 «hashcat!»
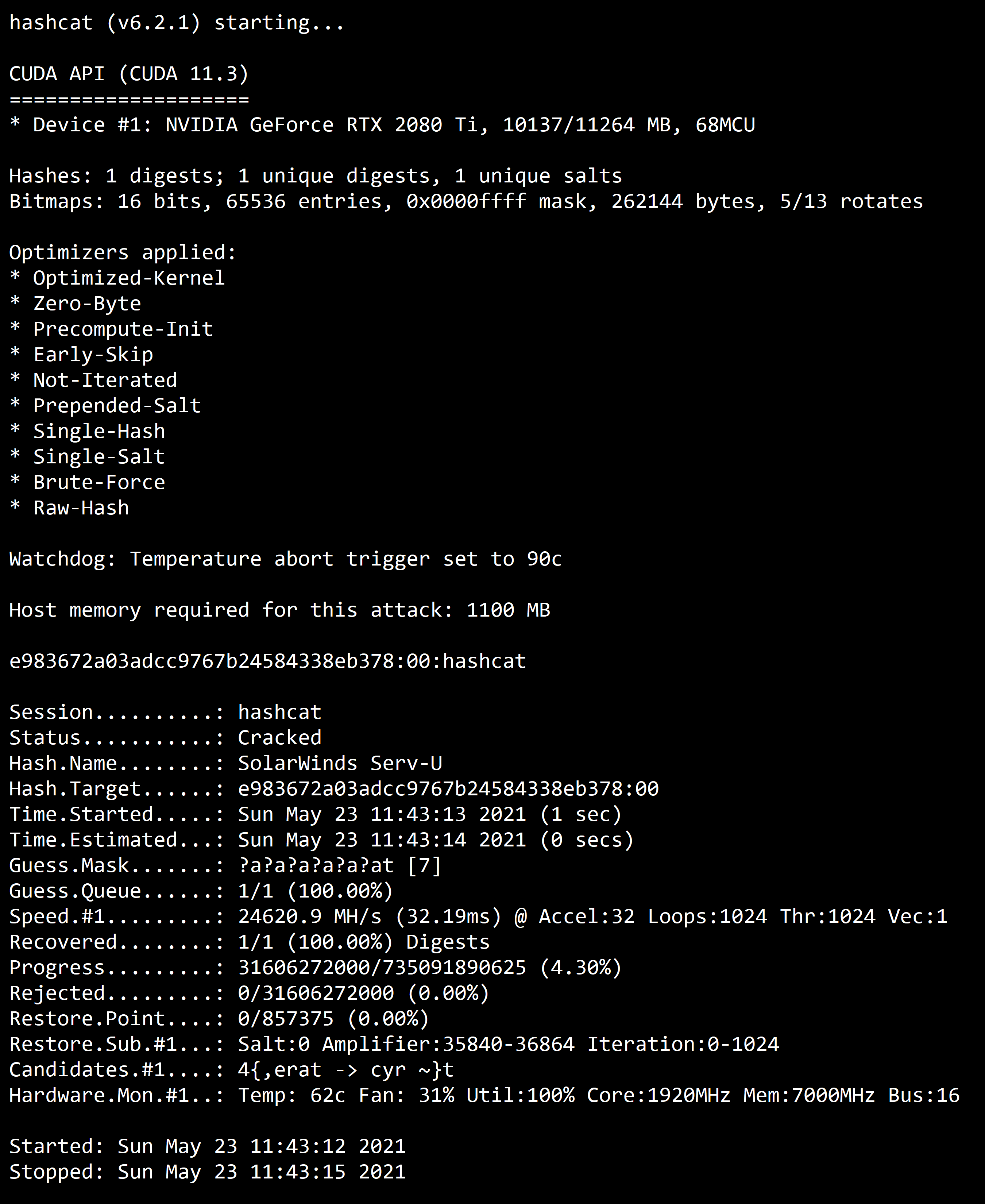
We expect a result similar like this:
In that case, everything is fine.
Successfully retrieving a PSK depend
- on the quality of the cap file,
- on the quality of the conversion tool,
- on the quality of the wordlist,
- and hashcat.
Источник